Problema
Per proteggere la rete da vulnerabilità come i ransomware si rende necessario disabilitare SMBv1 ed attivare il Digital Signing delle comunicazioni.
Anche InsightVM segnala queste vulnerabilità.
Fonti
SMBv1
https://docs.microsoft.com/en-us/windows-server/storage/file-server/troubleshoot/detect-enable-and-disable-smbv1-v2-v3
Digital Signing
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/microsoft-network-server-digitally-sign-communications-always
Disabilitare SMBv1
Mediante le GPO editare
Computer configuraton – Preferences – Windows Settings – Registry
e creare tre chiavi di registro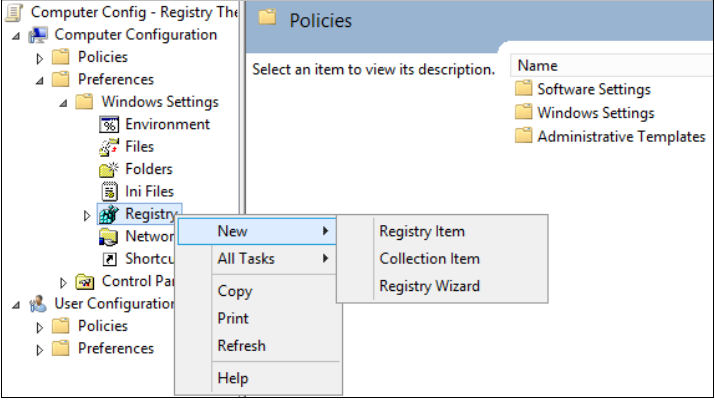
Disabilitare SMBv1 server
Action: Create
Hive: HKEY_LOCAL_MACHINE
Key Path: SYSTEMCurrentControlSetServicesLanmanServerParameters
Value name: SMB1
Value type: REG_DWORD
Value data: 0
Disabilitare SMBv1 client
Action: Update
Hive: HKEY_LOCAL_MACHINE
Key Path: SYSTEMCurrentControlSetservicesmrxsmb10
Value name: Start
Value type: REG_DWORD
Value data: 4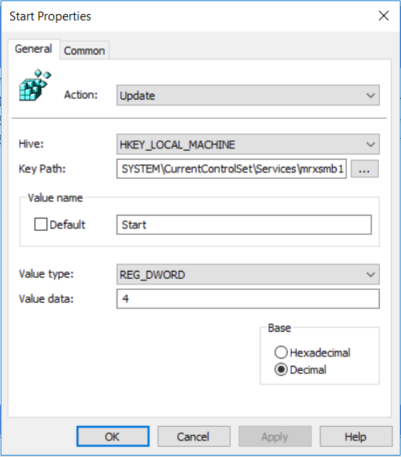
Rimuovere le dipendenze dal servizio MRxSMB10 appena disabilitato
Action: Replace
Hive: HKEY_LOCAL_MACHINE
Key Path: SYSTEMCurrentControlSetServicesLanmanWorkstation
Value name: DependOnService
Value type: REG_MULTI_SZ
Value data:
Bowser
MRxSmb20
NSI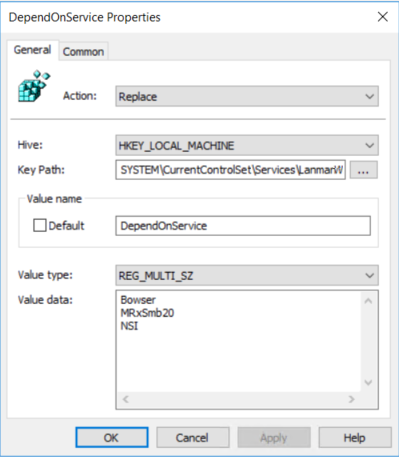
Abilitare la Digital Signing delle comunicazioni
Mediante le GPO editare
Computer configuraton – Policies – Windows Settings – Security Settings – Local Policies – Security Options
Abilitare "Microsoft network server: Digitally sign communication (always)"
